Blog
CMMC Timeline Update - 32 CFR Final Rule Sent For Final Review
On June 27, 2024 the CMMC Program Final Rule (32 CFR) has moved to the last step prior to finalization and publication. The rule is now in OIRA (Office of Information and Regulatory Affairs) review. This is the last step before publication in the federal register.
Defense Contractors and The Cloud: Which version of Microsoft 365 is right for you?
In the age of CMMC and pending independent third-party assessments of defense contractors’ compliance with their contractual cybersecurity obligations, there is a lot of misinformation out there about which Microsoft 365 environment meets your regulatory compliant needs. As a Microsoft Direct CSP and Azure Government CSP partner, we (Ariento) figured we’d address the most frequent questions our team receives when working with clients on their government cyber compliance journey. Note: a lot of this evaluation can be applied to other public cloud service providers (e.g. Google, Zoom, Google, Amazon, etc.) as well.
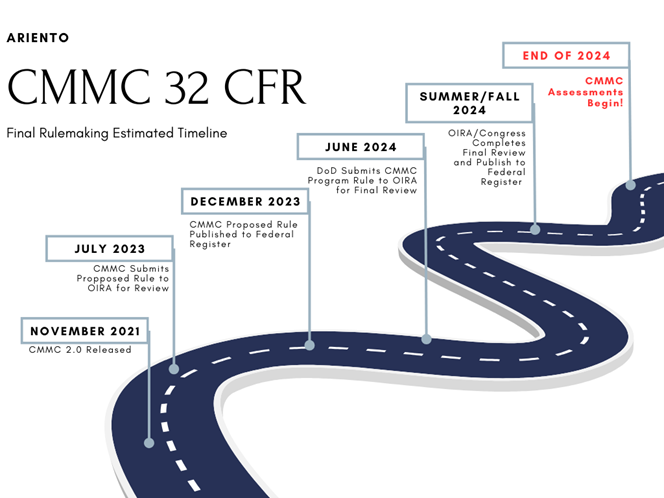
CMMC Timeline Update: DoD Submits CMMC Program to Office of Management and Budget for Review
On July 24th, the Department of Defense submitted the Cybersecurity Model Maturity Certification (CMMC) Program to the Office of Management and Budget (OMB) for review. So, what exactly does this mean for Defense contractors and when would a CMMC certification requirement start to show up in contracts solicitations?
DOJ’s False Claims Act and why it matters to Defense Contractors
On April 27, 2022, Aerojet Rocketdyne agreed to pay roughly $9 million to settle a False Claims Act complaint relating to overstated levels of cybersecurity compliance and controls. The case is significant because it is the first time that a whistleblower has successfully used the False Claims Act to hold a defense contractor accountable for cybersecurity fraud. The case also sets an important precedent for future whistleblowers who are trying to hold defense contractors accountable for cybersecurity violations.
An FAQ Guide to the CMMC (Pilot) Joint Surveillance Program
With news that the Cybersecurity Maturity Model Certification (CMMC) implementation is being pushed back (again) to 2024, the CMMC pilot program (called Joint Surveillance) becomes ever more important as it is the only option for organizations that desire to be a first mover in receiving their CMMC certification. At last check, there have been a total of seven completed assessments under the pilot program, and while that may seem low, interest is clearly high as our CMMC Third Party Assessor Organization (C3PAO) teams continue to receive questions about the program from Organizations Seeking Certification (OSC). This blog post addresses the most common questions we have seen.
What CMMC can and should learn from FedRAMP
In our role as NIST 800 series and Risk Management Framework (RMF) subject matter experts, we’ve worked closely with both third-party assessment organizations (3PAO) and companies at different points of the packaging process for Federal Risk and Authorization Management Program (FedRAMP) authorization.
CMMC – The Cyber Compliance Standard We’ve Been Waiting For?
Is the DoD’s new Cybersecurity Maturity Model Certification (CMMC) the future, or just another compliance initiative in the long line of competing cyber standards across a fragmented landscape. One thing is certain, this is a different approach.
CCH Cloud Systems Outage
Given our status as an affinity partner of CalCPA providing services to many CPA clients, we’ve had quite a few people reach out today with concerns about CCH cloud systems being down and the lack of communication from Wolters Kluwer. While there isn’t much, here is what we do know:
Why Military Veterans Are Well-Suited to Solve Our Economy’s Biggest Problem
The American economy is in jeopardy, and most people don’t even know it. Small businesses account for 99% of all U.S. businesses. They employ 60% of Americans and are responsible for more than half of the United States gross domestic product (GDP). In 2015, 62% of all data breaches were of small to medium sized businesses per Symantec, and 60% of those businesses were forced to close their doors within 6 months of being attacked. These statistics are scary, and indicate we are one major cyber-attack away from an economic crisis. So how do we fix this?
What Should You Do When You Think You’ve Been Hacked?
There are two questions I get from business owners all the time:
- How do I know if I've been hacked?
- What do I do if I have been hacked?
The answer to question 1 for many small businesses and individuals is